[ad_1]
Cybersecurity and information privateness are continuously within the information. Governments are passing new cybersecurity legal guidelines. Corporations are investing in cybersecurity controls comparable to firewalls, encryption and consciousness coaching at file ranges.
And but, individuals are dropping floor on information privateness.
In 2024, the Identification Theft Useful resource Heart reported that corporations despatched out 1.3 billion notifications to the victims of knowledge breaches. That is greater than triple the notices despatched out the yr earlier than. It is clear that regardless of rising efforts, private information breaches are usually not solely persevering with, however accelerating.
What are you able to do about this example? Many individuals consider the cybersecurity challenge as a technical drawback. They’re proper: Technical controls are an essential a part of defending private data, however they don’t seem to be sufficient.
As a professor of knowledge expertise, analytics and operations on the College of Notre Dame, I research methods to guard private privateness.
Stable private privateness safety is made up of three pillars: accessible technical controls, public consciousness of the necessity for privateness, and public insurance policies that prioritize private privateness. Every performs an important function in defending private privateness. A weak point in anybody places all the system in danger.
The primary line of protection
Know-how is the primary line of protection, guarding entry to computer systems that retailer information and encrypting data because it travels between computer systems to maintain intruders from gaining entry. However even the very best safety instruments can fail when misused, misconfigured or ignored.
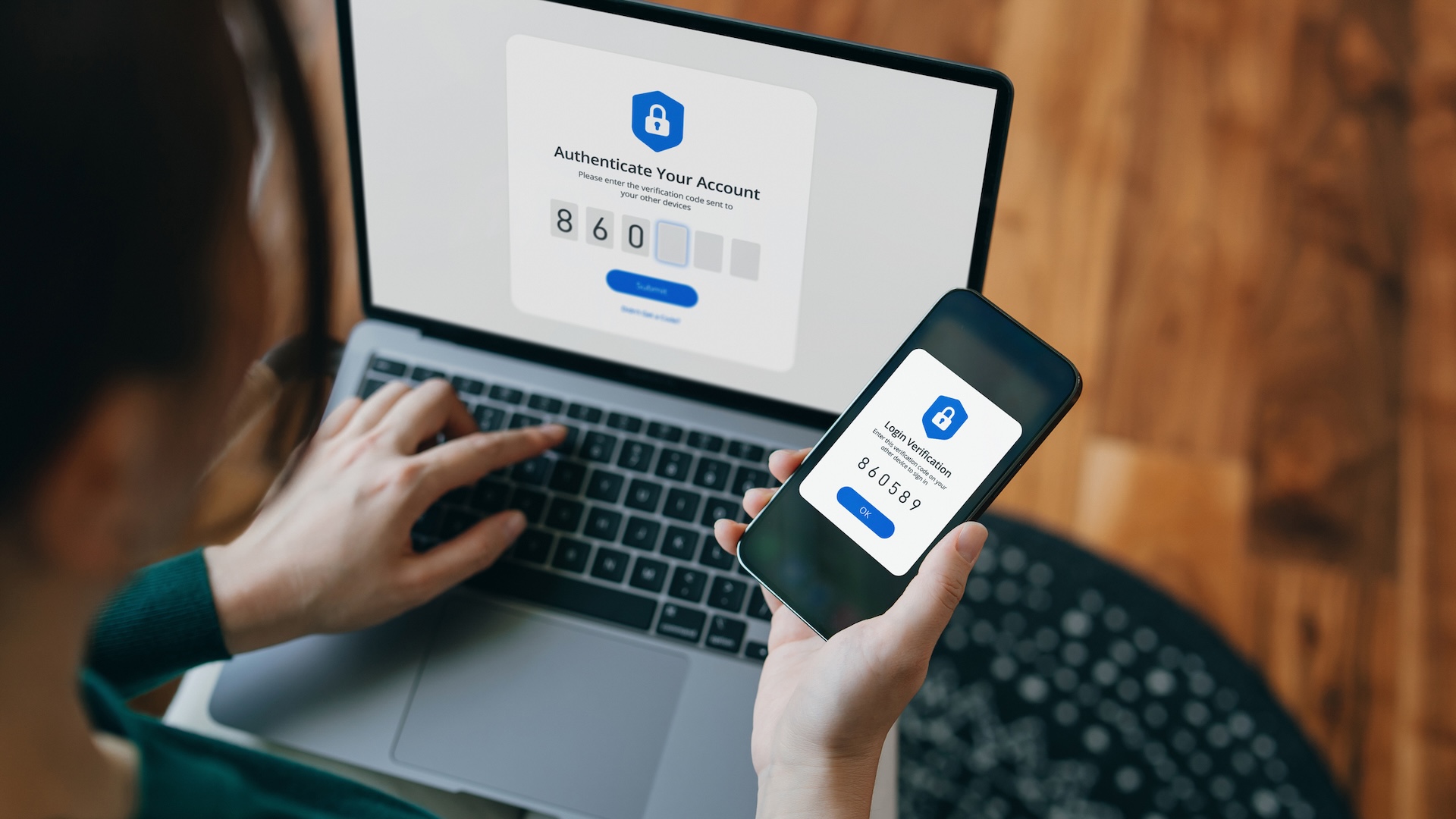
Two technical controls are particularly essential: encryption and multifactor authentication. These are the spine of digital privateness — they usually work finest when broadly adopted and correctly carried out.
Encryption makes use of complicated math to place delicate information in an unreadable format that may solely be unlocked with the fitting key. For instance, your net browser makes use of HTTPS encryption to guard your data whenever you go to a safe webpage. This prevents anybody in your community — or any community between you and the web site — from eavesdropping in your communications. At this time, almost all net site visitors is encrypted on this manner.
Associated: Quantum computer systems shall be a dream come true for hackers, risking the whole lot from army secrets and techniques to financial institution data. Can we cease them?
But when we’re so good at encrypting information on networks, why are we nonetheless struggling all of those information breaches? The truth is that encrypting information in transit is just a part of the problem.
Securing saved information
We additionally want to guard information wherever it is saved — on telephones, laptops and the servers that make up cloud storage. Sadly, that is the place safety usually falls brief. Encrypting saved information, or information at relaxation, is not as widespread as encrypting information that’s shifting from one place to a different.
Whereas fashionable smartphones sometimes encrypt recordsdata by default, the identical cannot be stated for cloud storage or firm databases. Solely 10% of organizations report that at the very least 80% of the data they’ve saved within the cloud is encrypted, in line with a 2024 {industry} survey. This leaves an enormous quantity of unencrypted private data doubtlessly uncovered if attackers handle to interrupt in. With out encryption, breaking right into a database is like opening an unlocked submitting cupboard — the whole lot inside is accessible to the attacker.
Multifactor authentication is a safety measure that requires you to supply multiple type of verification earlier than accessing delicate data. One of these authentication is harder to crack than a password alone as a result of it requires a mix of several types of data. It usually combines one thing you already know, comparable to a password, with one thing you could have, comparable to a smartphone app that may generate a verification code or with one thing that is a part of what you’re, like a fingerprint. Correct use of multifactor authentication reduces the chance of compromise by 99.22%.
Whereas 83% of organizations require that their workers use multifactor authentication, in line with one other {industry} survey, this nonetheless leaves thousands and thousands of accounts protected by nothing greater than a password. As attackers develop extra refined and credential theft stays rampant, closing that 17% hole is not only a finest apply — it is a necessity.
Multifactor authentication is among the easiest, handiest steps organizations can take to stop information breaches, nevertheless it stays underused. Increasing its adoption might dramatically scale back the variety of profitable assaults annually.
Consciousness provides folks the information they want
Even the very best expertise falls brief when folks make errors. Human error performed a task in 68% of 2024 information breaches, in line with a Verizon report. Organizations can mitigate this danger by worker coaching, information minimization — that means gathering solely the data mandatory for a process, then deleting it when it is not wanted — and strict entry controls.
Insurance policies, audits and incident response plans may also help organizations put together for a doable information breach to allow them to stem the injury, see who’s accountable and be taught from the expertise. It is also essential to protect towards insider threats and bodily intrusion utilizing bodily safeguards comparable to locking down server rooms.
Public coverage holds organizations accountable
Authorized protections assist maintain organizations accountable in preserving information protected and giving folks management over their information. The European Union’s Common Knowledge Safety Regulation is among the most complete privateness legal guidelines on the earth. It mandates robust information safety practices and offers folks the fitting to entry, right and delete their private information. And the Common Knowledge Safety Regulation has tooth: In 2023, Meta was fined €1.2 billion (US$1.4 billion) when Fb was present in violation.
Regardless of years of debate, the U.S. nonetheless has no complete federal privateness regulation. A number of proposals have been launched in Congress, however none have made it throughout the end line. As a substitute, a mixture of state laws and industry-specific guidelines — such because the Well being Insurance coverage Portability and Accountability Act for well being information and the Gramm-Leach-Bliley Act for monetary establishments — fill the gaps.
Some states have handed their very own privateness legal guidelines, however this patchwork leaves People with uneven protections and creates compliance complications for companies working throughout jurisdictions.
The instruments, insurance policies and information to guard private information exist — however folks’s and establishments’ use of them nonetheless falls brief. Stronger encryption, extra widespread use of multifactor authentication, higher coaching and clearer authorized requirements might forestall many breaches. It is clear that these instruments work. What’s wanted now’s the collective will — and a unified federal mandate — to place these protections in place.
This text is a part of a sequence on information privateness that explores who collects your information, what and the way they accumulate, who sells and buys your information, what all of them do with it, and what you are able to do about it.
This edited article is republished from The Dialog underneath a Inventive Commons license. Learn the unique article.
[ad_2]

