The FDA launched their up to date steerage on Cybersecurity in medical gadgets: High quality System Concerns and content material for Premarket submissions on the finish of June in 2025. On this steerage the FDA emphasizes the expectation that cybersecurity dangers and vulnerabilities be addressed in a menace mannequin. Cybersecurity procedures to help merchandise from preliminary design to finish of life should be applied. Sufficient cybersecurity protections should be addressed within the design inputs throughout improvement and never “bolted on” after improvement is accomplished.
If you’re a developer or producer that’s or shall be liable for a linked medical system, the cybersecurity course of is one thing it’s good to make investments effort in now.
There are a number of requirements reminiscent of ANSI/AAMI SW96:2023 and IEC 81001-5-1: 2021 which might be well known within the US and within the EU that element what actions and deliverables must be addressed relative to cybersecurity threat evaluation for medical system software program. This quick article is targeted on find out how to carry out the evaluation which is the core a part of the cybersecurity menace mannequin. The target for this text is to offer perception on conducting safety threat evaluation that’s impactful for the entire lifetime of a medical system or medical system software program.
Machine cybersecurity planning
From a pre-market perspective, the important thing components to a safety evaluation are as follows:
Determine 1 – Cybersecurity steps in threat evaluation
Along with planning for cybersecurity medical system firms now have to implement a selected framework of their high quality system. To catch up to a degree of compliance some firms are making the error of addressing compliance by investing in a one-tool-does-all software program choice, however this will seemingly miss the true wants to handle cybersecurity in your group. The wholistic resolution is an software of a Safe Product Improvement Framework that addressed the actions and duties all through the whole product lifecycle (TPLC). Commissioning sources to develop and replace processes and SOP’s is required however the core of getting a stable course of is to determine an efficient and environment friendly threat evaluation methodology. The chance evaluation methodology is represented because the Safety Danger Evaluation within the evaluation part of determine 1.
Deal with Belongings in Safety Evaluation Desk
The Safety Danger Evaluation is used to establish potential safety threat controls and establish vulnerabilities. Two tables must be established, a Danger Evaluation desk that identifies and maintains the safety threat controls and the continuing vulnerabilities desk monitoring the present vulnerabilities. The 2 evaluation tables might be in separate tabs on a easy spreadsheet as they’ve filtering and sorting capabilities to permit for long run administration of the tables. The content material for the Danger Evaluation Desk is mirrored in Desk 1 addressing the Safety Controls.

Desk 1 – Safety Danger Evaluation evaluation desk
The main target of the Safety Danger Evaluation must be the belongings outlined within the safety structure and the way threats could exploit vulnerabilities to compromise the belongings.
The belongings are components which might be of worth to the person, affected person, person group and enterprise which might be related to safety. Belongings would possibly usually embody:
- Knowledge dealt with and saved on the product (e.g., Logs, buyer or operational information, configuration information)
- Knowledge of private nature (e.g., Protected Well being Data/PHI)
- Credential info (e.g., passwords, credentials, keys)
- Software program/firmware of the product
- Third social gathering providers (e.g., cloud providers, open supply libraries, API’s).
The evaluation ought to embody fairly sensible threats to every of the belongings. The STRIDE mannequin might be utilized to establish the potential menace in every evaluation row. The requirements STRIDE mannequin, and the specified safety property is supplied in Desk 2 beneath.
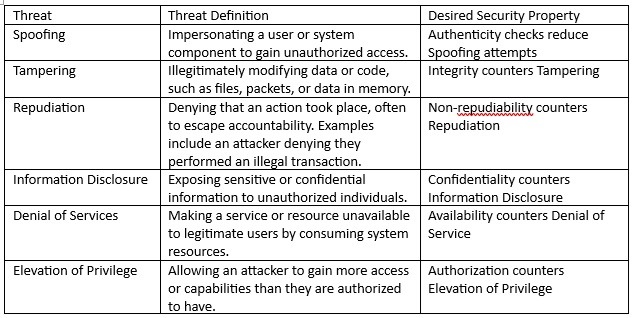
Desk 2 – Stride definitions
Vulnerability identification
Along with the Safety Danger Evaluation the separate ongoing vulnerabilities desk must be maintained, as talked about beforehand. This desk comprises the identified vulnerabilities which have been recognized within the system. Vulnerabilities are flaws or weaknesses that could possibly be exploited by the potential threat-sources. Vulnerabilities might be recognized via:
- Figuring out vulnerabilities within the Safety Danger Evaluation
- cybersecurity penetration evaluation and testing of the product
- via static evaluation scanning of internally developed software program with SAST (Static Utility Safety Testing) software
- via a dynamic evaluation scanning with DAST (Dynamic Utility Safety Testing) software
- reviewing current catalogs just like the Frequent Vulnerabilities and Publicity Record, the Nationwide Vulnerability Database (NVD), the Nationwide Well being ISAC, and launch notes of SOUP/COTS.
- recognized via vulnerability scanning utilizing a SCA (Software program Composition Evaluation) software for OTS or open-source elements.
The analysis of identified vulnerabilities is critical previous to any product launch and maintained till the product is retired. As vulnerabilities are recognized and addressed, they could be faraway from the continuing vulnerabilities evaluation desk. Actions on the vulnerabilities are pushed by a severity willpower of the vulnerability and the CVSS rating. The CVSS scoring mannequin identifies six base gadgets in its matrix for every of the recognized vulnerabilities: Assault Vector (AV), Assault Complexity (AC), Privileges Required (PR), Person Interplay (UI), Scope (S) and Impression (CIA) measuring confidentiality, integrity and availability loss.
Decide affect of threats
In security threat evaluation we all know that threat is the mixture of severity and chance of hurt (Danger = P x S). Nonetheless, for safety threat evaluation the FDA recommends contemplating the exploitability of a possible vulnerability versus the usage of chance of an assault occurring with success. Exploitability must be based mostly on how susceptible a system is to being compromised. The higher the safety controls the decrease the danger. The acceptability analysis of threats to belongings and vulnerabilities must be pushed by a desk matrix like to at least one in Desk 3, pushed by severity of hurt and exploitability.
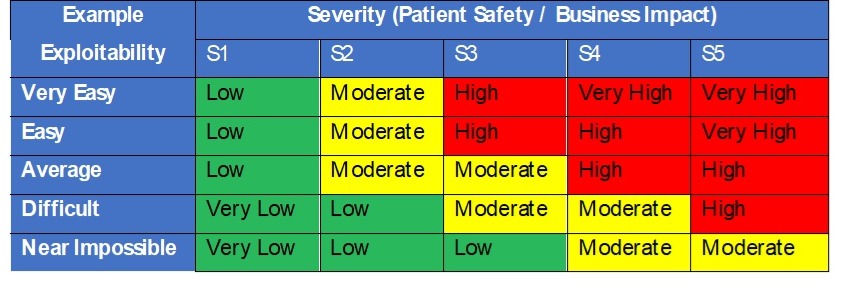
Desk 3 – Safety exploitability and severity determination desk
Larger dangers would require documented threat controls within the Safety Danger Evaluation desk to cut back their exploitability and total threat. Danger controls ought to then drive necessities within the design and are subsequently verified as efficient throughout design verification.
Conclusion
The safety evaluation of dangers and vulnerabilities must be maintained in two tables, as one is required to establish and preserve the safety dangers and the opposite is an ongoing checklist of vulnerabilities that require periodic updates after launch. These two evaluation tables are to be up to date periodically and the continuing vulnerability checklist drive patch and buyer notification throughout product upkeep.
Whether or not your organization could also be simply beginning out or at the next level within the cybersecurity maturity spectrum of reaching a sturdy and environment friendly cybersecurity framework, a concentrate on the format and evaluation core practices as a precedence and can result in higher choices on instruments and enhancements within the course of effectivity and competency.
Photograph: Traitov, Getty Pictures
Bob Barrett, vp of techniques engineering at Full Spectrum, is an skilled engineering chief and group builder with a concentrate on outcomes. He has technical strengths gained from greater than 30 years in medical system techniques engineering, techniques and software program validation, security threat evaluation, high quality administration and undertaking administration. Bob spent 15 years with Baxter’s drug supply division, the place he led the techniques engineering group. Bob has the position of participant coach at Full Spectrum, main the techniques engineering group, whereas offering his deep insights on to purchasers. Bob is a robust believer in cadence pushed undertaking administration methods. His potential to be hands-on or lead cross-functional groups accelerates shopper’s medical improvement packages from idea to market launch.
This put up seems via the MedCity Influencers program. Anybody can publish their perspective on enterprise and innovation in healthcare on MedCity Information via MedCity Influencers. Click on right here to learn how.


