Quantum computer systems are coming. And after they arrive, they’ll upend the way in which we shield delicate information.
Not like classical computer systems, quantum computer systems harness quantum mechanical results — like superposition and entanglement — to course of and retailer information in a kind past the 0s and 1s which are digital bits. These “quantum bits” — or qubits — may open up large computing energy.
“Like many highly effective applied sciences, you should use [quantum computing] for excellent good,” Rebecca Krauthamer, a technological ethicist and CEO of cybersecurity agency QuSecure, instructed Dwell Science. “And you can too use it for malicious functions.”
When usable quantum computer systems first come on-line, most individuals — and even most giant organizations — will nonetheless depend on classical computer systems. Cryptographers subsequently must provide you with methods to guard information from highly effective quantum computer systems, utilizing packages that may run on a daily laptop computer.
That is the place the sector of post-quantum cryptography is available in. A number of teams of scientists are racing to develop cryptographic algorithms that may evade hacking by quantum computer systems earlier than they’re rolled out. A few of these cryptographic algorithms depend on newly developed equations, whereas others are turning to centuries-old ones. However all have one factor in frequent: They cannot be simply cracked by algorithms that run on a quantum pc.
“It is like a basis for a three-story constructing, after which we constructed a 100-story skyscraper on it.”
Michele Mosca, co-founder and CEO of cybersecurity firm evolutionQ
The foundations of cryptography
Cryptography dates again 1000’s of years; the earliest recognized instance is a cipher carved into historic Egyptian stone in 1900 B.C. However the cryptography utilized by most software program methods immediately depends on public key algorithms. In these methods, the pc makes use of algorithms — which regularly contain factoring the product of two giant prime numbers — to generate each a public key and a non-public key. The general public key’s used to scramble the info, whereas the non-public key, which is offered solely to the sender, can be utilized to unscramble the info.
To crack such cryptography, hackers and different malefactors typically should issue the merchandise of very giant prime numbers or attempt to discover the non-public key by brute pressure — basically throwing out guesses and seeing what sticks. It is a arduous drawback for classical computer systems as a result of they’ve to check every guess one after one other, which limits how rapidly the components may be recognized.

A 100-story skyscraper on a three-story constructing
These days, classical computer systems typically sew collectively a number of encryption algorithms, applied at completely different places, akin to a tough disk or the web.
“You’ll be able to consider algorithms like constructing bricks,” Britta Hale, a pc scientist on the Naval Postgraduate College, instructed Dwell Science (Hale was talking strictly in her capability as an skilled and never on behalf of the varsity or any group.) When the bricks are stacked, each makes up a small piece of the fortress that retains out hackers.
However most of this cryptographic infrastructure was constructed on a basis developed within the Nineteen Nineties and early 2000s, when the web was a lot much less central to our lives and quantum computer systems had been primarily thought experiments. “It is like a basis for a three-story constructing, after which we constructed a 100-story skyscraper on it,” Michele Mosca, co-founder and CEO of cybersecurity firm evolutionQ, instructed Dwell Science. “And we’re form of praying it is OK.”
It would take a classical pc 1000’s and even billions of years to crack a extremely arduous prime factorization algorithm, however a strong quantum pc can typically clear up the identical equation in a couple of hours. That is as a result of a quantum pc can run many calculations concurrently by exploiting quantum superposition, wherein qubits can exist in a number of states directly. In 1994, American mathematician Peter Shor confirmed that quantum computer systems can effectively run algorithms that may rapidly clear up prime-number factoring issues. Consequently, quantum computer systems may, in idea, tear down the cryptographic fortresses we presently use to guard our information.
Put up-quantum cryptography goals to exchange out of date constructing blocks with less-hackable bricks, piece by piece. And step one is to seek out the suitable math issues to make use of. In some instances, which means returning to equations which have been round for hundreds of years.
At the moment, the Nationwide Institute of Requirements and Expertise (NIST) is taking a look at 4 issues as potential foundations for post-quantum cryptography. Three belong to a mathematical household often called structured lattices. These issues ask questions in regards to the vectors — mathematical phrases that describe path and magnitude between interconnected nodes — just like the connection factors in a spiderweb, Mosca mentioned. These lattices can theoretically have an infinite variety of nodes and exist in a number of dimensions.
Specialists imagine lattice issues can be arduous for a quantum pc to crack as a result of, not like another cryptographic algorithms, lattice issues do not depend on factoring large numbers.
As a substitute, they use the vectors between nodes to create a key and encrypt the info. Fixing these issues could contain, for instance, calculating the shortest vector within the lattice, or attempting to find out which vectors are closest to at least one one other. In case you have the important thing — typically a “good” beginning vector — these issues could also be comparatively simple. However with out that key, they’re devilishly arduous. That is as a result of nobody has devised an algorithm, like Shor’s algorithm, that may effectively clear up these issues utilizing quantum computing structure.
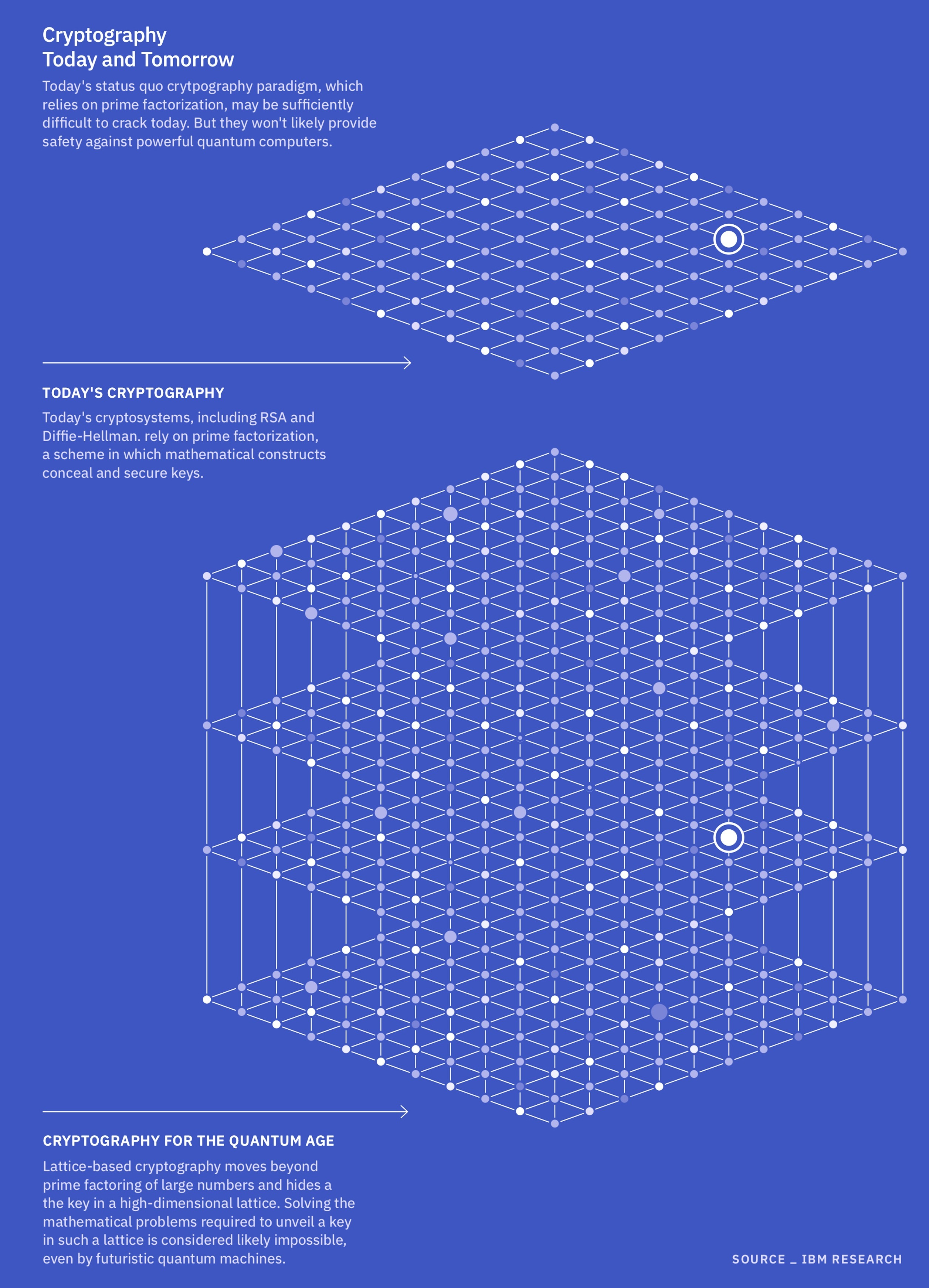
The fourth drawback that NIST is contemplating belongs to a bunch known as hash capabilities. Hash capabilities work by taking the digital key for unlocking a particular level on an information desk, scrambling that key and compressing it right into a shorter code. This kind of algorithm is already a cornerstone of recent cybersecurity, so in idea, it needs to be extra simple to improve classical computer systems to a quantum-proof model in contrast with different post-quantum cryptographic schemes, Mosca mentioned. And equally to structured lattices, they can not simply be solved by brute pressure alone; you want some clue as to what is going on on contained in the “black field” key generator to determine them out throughout the age of the universe.
However these 4 issues do not cowl the entire doubtlessly quantum-safe algorithms in existence. For instance, the European Fee is taking a look at an error-correcting code often called the McEliece cryptosystem. Developed greater than 40 years in the past by American engineer Robert McEliece, this technique makes use of random quantity era to create a private and non-private key, in addition to an encryption algorithm. The recipient of the non-public key makes use of a set cipher to decrypt the info.
McEliece encryption is basically thought-about each quicker and safer than probably the most generally used public-key cryptosystem, known as Rivest-Shamir-Adleman. As with a hash operate, would-be hackers want some perception into its black-box encryption to unravel it. On the plus aspect, consultants think about this technique very protected; on the draw back, even the keys to unscramble the info should be processed utilizing extraordinarily giant, cumbersome matrices, requiring plenty of vitality to run.
An analogous error-correcting code, often called Hamming Quasi-Cyclic (HQC), was just lately chosen by NIST as a backup to its major candidates. Its major benefit over the basic McEliece system is that it makes use of smaller key and ciphertext sizes.
One other sort of algorithm that generally comes up in conversations about post-quantum cryptography is the elliptic curve, Bharat Rawal, a pc and information scientist at Capitol Expertise College in Maryland, instructed Dwell Science. These issues return no less than to historic Greece. Elliptic curve cryptography exploits primary algebra — calculating the factors on a curved line — to encrypt keys. Some consultants imagine a brand new elliptic curve algorithm may evade hacking by a quantum pc. Nonetheless, others argue {that a} hacker may hypothetically use Shor’s algorithm on a quantum pc to interrupt most recognized elliptic curve algorithms, making them a less-secure choice.
No silver bullet
Within the race to seek out quantum-safe cryptographic equations, there will not be a silver bullet or a one-size-fits-all answer. For instance, there’s all the time a trade-off in processing energy; it would not make a lot sense to make use of complicated, power-hungry algorithms to safe low-priority information when an easier system is likely to be completely ample.
“It isn’t like one algorithm [combination] would be the technique to go; it will depend on what they’re defending,” Hale mentioned.
The truth is, it is beneficial for organizations that use classical computer systems to have multiple algorithm that may shield their information from quantum threats. That approach, “if one is confirmed to be weak, you may simply swap to at least one that was not confirmed weak,” Krauthamer mentioned. Krauthamer’s workforce is presently working with the U.S. Military to enhance the group’s skill to seamlessly swap between quantum-safe algorithms — a function often called cryptographic agility.
Despite the fact that helpful (or “cryptographically related”) quantum computer systems are nonetheless a number of years away, it is important to begin getting ready for them now, consultants mentioned. “It might probably take a few years to improve current methods to be prepared for post-quantum cryptography,” Douglas Van Bossuyt, a methods engineer on the Naval Postgraduate College, instructed Dwell Science in an electronic mail. (Van Bossuyt was talking strictly as a subject-matter skilled and never on behalf of the Naval Postgraduate College, the Navy or the Division of Protection.) Some methods are powerful to improve from a coding standpoint. And a few, akin to these aboard navy craft, may be tough — and even unimaginable — for scientists and engineers to entry bodily.
Different consultants agree that post-quantum cryptography is a urgent difficulty. “There’s additionally the prospect that, once more, as a result of quantum computer systems are so highly effective, we can’t really know when a company will get entry to such a strong machine,” Krauthamer mentioned.
There’s additionally the specter of “harvest-now, decrypt-later” assaults. Malicious actors can scoop up delicate encrypted information and reserve it till they’ve entry to a quantum pc that is able to cracking the encryption. All these assaults can have a variety of targets, together with financial institution accounts, private well being data and nationwide safety databases. The earlier we will shield such information from quantum computer systems, the higher, Van Bossuyt mentioned.
And as with every cybersecurity strategy, post-quantum cryptography will not signify an finish level. The arms race between hackers and safety professionals will proceed to evolve properly into the long run, in ways in which we will solely start to foretell. It could imply creating encryption algorithms that run on a quantum pc versus a classical one or discovering methods to thwart quantum synthetic intelligence, Rawal mentioned.
“The world must hold engaged on this as a result of if these [post-quantum equations] are damaged, we do not need to wait 20 years to provide you with the substitute,” Mosca mentioned.

